KNX Topology Troubleshooting with ETS Tools
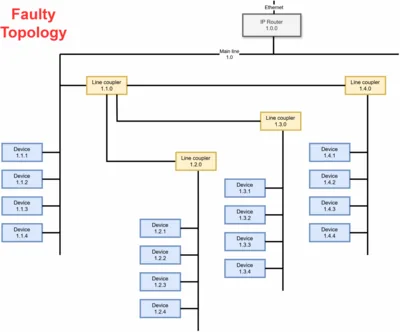
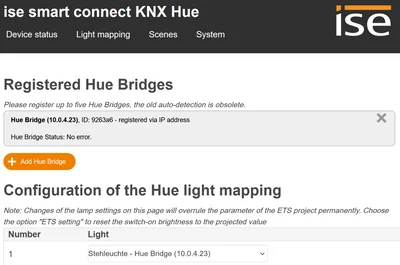
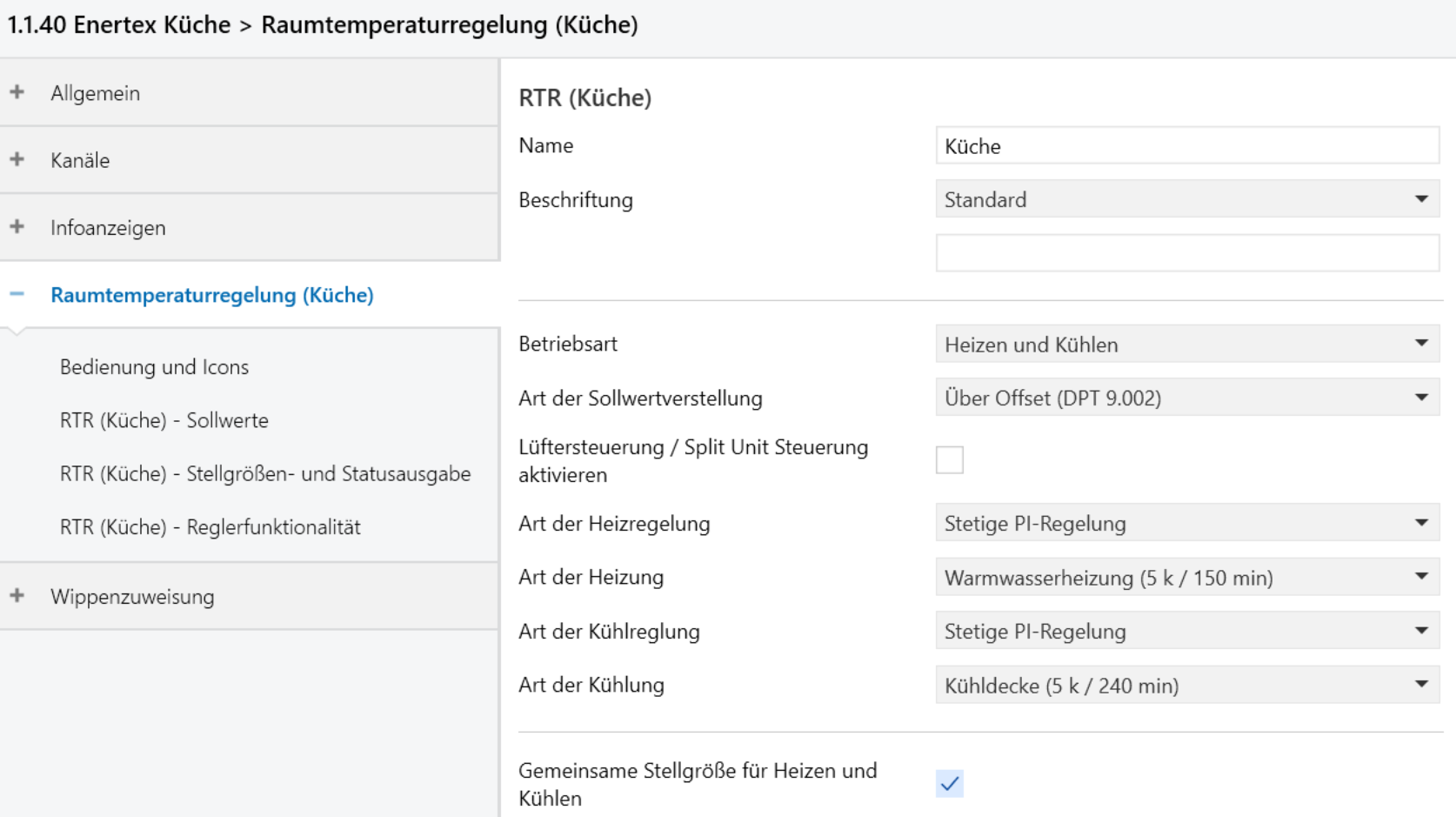
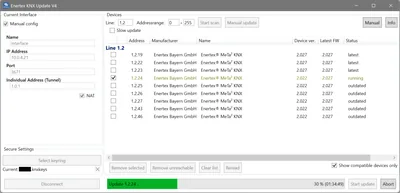
This article shows how to check your KNX installation’s topology with the tools provided by ETS. You can run through all the verifications from your desk without having to deal with the physical wiring.
KNX & ETS