Determining the Size of a Folder without Access or Permissions
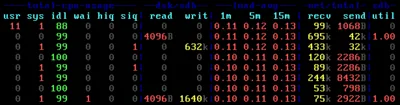
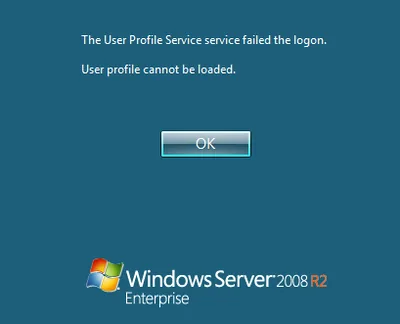
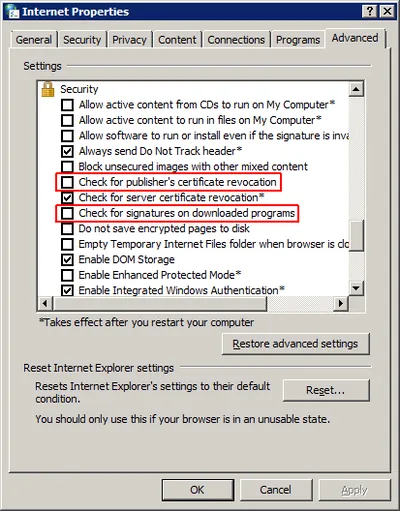
Imagine you need to determine the size of a directory, but you do not have access to it and cannot change the permissions, either. Such a situation is common with Windows user profiles. This article shows how to deal with it.
User Profiles