VMware Horizon in a Lab: Getting Rid of SSL Errors
- Citrix/Terminal Services/Remote Desktop Services
- Published Feb 17, 2016
This is a description of a quick and dirty way to get SSL to work correctly in a VMware Horizon View installation in a lab environment. Do not do this in production!
The Situation
The Horizon View Connection Server installer creates a self-signed certificate which it places in the computer’s personal certificate store. This certificate’s root is not trusted by anyone, least of all by the clients trying to connect to your apps and desktops.
Establishing Trust
To make the default self-signed certificate work correctly you need to export it from the computer’s personal certificate store and then re-import it in the trusted root certificate store.
Exporting
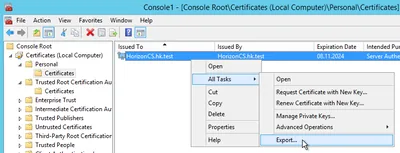
It is OK to export without a private key; leave the file format at the default.
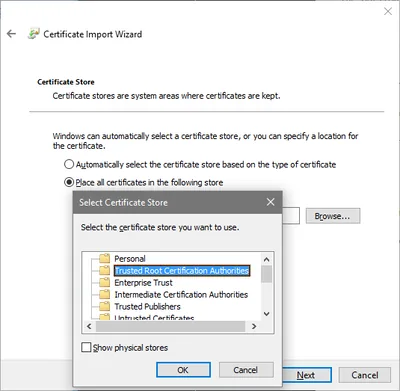
Importing - Connection Server
When re-importing the key on the Horizon View Connection Server manually select the computer’s Trusted Root Certification Authorities store:
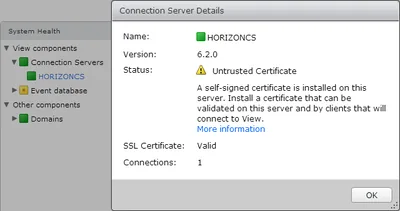
After the import restart the Connection Server machine. View Administrator should now display the Connection Server status in green (certificate valid):
Importing - Clients
Clients that connect to Horizon need the certificate imported as trusted root certificate in the same way as described for the Connection Server above.
Name Resolution
Clients connecting to Horizon View need to be able to resolve the name as it is stored in the certificate, in all likelihood fully qualified. If your (lab) clients use a different DNS server than the Horizon installation the simplest solution is to add the Connection Server’s name and IP address to each client’s hosts file.





Comments