Finding (Executables in) User-Writeable Directories
- Security
- Published Jul 7, 2021
This article presents two different detection types for insecure filesystem permissions on Windows endpoints: scanning for directories that are user-writable, and detecting processes that are started from user-writeable directories.
Directory Scan With ListUserWriteableDirectories & SetACL
My ListUserWriteableDirectories script is an implementation of the first detection type: it scans the filesystem listing any permissions not known to be safe.
ListUserWriteableDirectories is powerful: by using SetACL for the actual scanning, it inherits SetACL’s cool features that make it possible to bypass permissions and scan every directory in the filesystem. ListUserWriteableDirectories is flexible: it has a configurable list of directories to exclude. It also has a list of users and groups that are considered safe and should be ignored in the scan. A third list specifies which write (or otherwise insecure) permissions to include in the report.
How Does It Work?
ListUserWriteableDirectories recursively traverses the filesystem. For every directory that is not excluded, it examines the access control entries (ACEs) looking for any of the configured insecure permissions. If an ACE’s permission matches, it checks the known-safe user/group exclusions. Any remaining ACEs are deemed insecure and included in the output.
ListUserWriteableDirectories checks for all kinds of insecure permissions, not just write access: full, change, write, write_owner, write_dacl, write_ea, write_attr, add_file.
How to Scan the Filesystem With ListUserWriteableDirectories
To recursively scan C:\ with ListUserWriteableDirectories and list directories with insecure permissions run the following command:
ListUserWriteableDirectories.ps1 -SetACLPath 'D:\Tools\SetACL\SetACL.exe' -ScanDirectory C:\ -IncludeInherited
(adjust the path to SetACL.exe as needed)
The output looks similar to the following:
"C:\Windows\System32\Microsoft\Crypto\RSA\MachineKeys","Everyone",write+read,no_inheritance
"C:\Windows\System32\spool\SERVERS","BUILTIN\Users",FILE_ADD_FILE+FILE_ADD_SUBDIRECTORY+FILE_READ_EA+FILE_READ_ATTRIBUTES,container_inherit
"C:\Windows\System32\Tasks","NT AUTHORITY\Authenticated Users",write+READ_CONTROL,container_inherit
Directory Scan With Sysinternals AccessChk
AccessChk vs. ListUserWriteableDirectories
AccessChk is another scanning tool, but it follows a slightly different approach than ListUserWriteableDirectories. Where the latter lists any access control entries not known to be safe, AccessChk evaluates a given user’s (or group’s) access, which the tool categorizes as read, write, both, or none. Command-line options allow filtering for write access, for example.
AccessChk is the tool of choice if you want to know which directories a given user or a specific group has access to. ListUserWriteableDirectories on the other hand should be used when you need to list any directories with insecure permissions.
How to Scan the Filesystem With AccessChk
To recursively scan C:\ with AccessChk and list directories with write access for the group Users run the following command:
accesschk64.exe -uwdqs Users c:\*
The output looks similar to the following:
RW c:\Program Files\Microsoft SQL Server\130\Shared\ErrorDumps
RW c:\Program Files\ViPER4Windows\DriverComm
RW c:\Program Files (x86)\Common Files\Adobe\SLCache
Process Start Detection With uberAgent ESA
vast limits’ uberAgent ESA endpoint security analytics product comes with built-in rules to detect processes that are started from user-writeable directories.
How Does It Work?
Whenever a process is started, uberAgent ESA determines the permissions of the executable’s directory. Next, it looks up the user of the session the process is a part of. Finally, uberAgent ESA calculates the session user’s effective permissions on the directory. If the user has write access, the corresponding activity monitoring rule is matched, which generates an event in the backend.
How to Detect Insecure Executable Permissions With uberAgent ESA
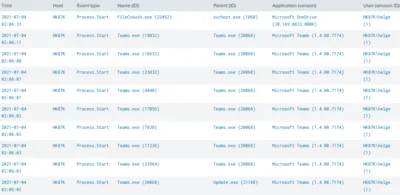
The detection of process starts from user-writeable directories is part of uberAgent ESA’s default feature set. Just install uberAgent ESA as documented. Once at least one endpoint is collecting data, head over to the uberAgent ESA Splunk dashboard Activity Monitoring Events. Select the tag proc-start-dir-user-writeable and you should see a table similar to the following:
More uberAgent ESA Magic: Process Directory SDDL Analysis
uberAgent ESA’s capability to detect process starts from user-writeable directories is a shortcut to the powerful underlying process directory permission analysis functionality. This makes the entire security descriptor available for regex matching in activity monitoring rules. In order to make SDDL useful for pattern-matching, uberAgent ESA performs two crucial steps:
- uberAgent ESA replaces SIDs with user/group names
- uberAgent ESA replaces hexadecimal access masks with human-readable permission names
Here’s an SSDL string before uberAgent ESA applied its magic:
O:S-1-5-80-956008885-3418522649-1831038044-1853292631-2271478464G:S-1-5-80-956008885-3418522649-1831038044-1853292631-2271478464D:PAI(A;;FA;;;S-1-5-80-956008885-3418522649-1831038044-1853292631-2271478464)(A;CIIO;GA;;;S-1-5-80-956008885-3418522649-1831038044-1853292631-2271478464)(A;;0x1301bf;;;SY)(A;OICIIO;GA;;;SY)(A;;0x1301bf;;;BA)(A;OICIIO;GA;;;BA)(A;;0x1200a9;;;BU)(A;OICIIO;GXGR;;;BU)(A;OICIIO;GA;;;CO)(A;;0x1200a9;;;AC)(A;OICIIO;GXGR;;;AC)(A;;0x1200a9;;;S-1-15-2-2)(A;OICIIO;GXGR;;;S-1-15-2-2)S:AINO_ACCESS_CONTROL
And here’s the same SDDL string after having been processed by uberAgent ESA:
O:NT SERVICE\TrustedInstallerG:NT SERVICE\TrustedInstallerD:PAI(A;;full;;;NT SERVICE\TrustedInstaller)(A;CIIO;full;;;NT SERVICE\TrustedInstaller)(A;;change;;;SY)(A;OICIIO;full;;;SY)(A;;change;;;BA)(A;OICIIO;full;;;BA)(A;;read_execute;;;BU)(A;OICIIO;read_execute;;;BU)(A;OICIIO;full;;;CO)(A;;read_execute;;;AC)(A;OICIIO;read_execute;;;AC)(A;;read_execute;;;APPLICATION PACKAGE AUTHORITY\ALL RESTRICTED APPLICATION PACKAGES)(A;OICIIO;read_execute;;;APPLICATION PACKAGE AUTHORITY\ALL RESTRICTED APPLICATION PACKAGES)S:AINO_ACCESS_CONTROL
Please see the documentation for a deconstruction and explanation of the above SDDL string format.





Comments