How to Enable BitLocker Hardware Encryption with SSDs
2019-10-01: with the 2019 September update KB4516045 BitLocker uses software instead of hardware encryption by default. Likely reason: the security of software encryption can be controlled by Microsoft. Hardware encryption in the drive may be buggy.
Beginning with Windows 8 BitLocker can offload the encryption from the CPU to the disk drive. But enabling that can be challenging. Here is how.
Why Use Hardware Encryption?
Doing encryption in hardware on the disk drive instead of in software by the CPU should be more effective. That translates into longer battery life and higher performance. AnandTech has some numbers that illustrate these points.
Requirements
These are the system requirements according to TechNet:
For data drives:
- The drive must be in an uninitialized state.
- The drive must be in a security inactive state.
If the drive is used as a startup drive the following apply additionally:
- The computer must always boot natively from UEFI.
- The computer must have the Compatibility Support Module (CSM) disabled in UEFI.
- The computer must be UEFI 2.3.1 based and have the EFI_STORAGE_SECURITY_COMMAND_PROTOCOL defined.
One very important thing is uninitialized state: it means that you cannot clone a drive with data on it and enable BitLocker with hardware encryption afterwards.
Problem: Intel Rapid Storage Technology Driver
What Microsoft does not list in their requirements is that older versions of the Intel Rapid Storage Technology Driver prevent hardware encryption. There is a 12-page thread in the Lenovo forums mainly about this problem. Version 13.2 of the RST driver fixes the issue, so make sure you have at least that version installed.
I would not recommend the alternative solution of not installing the RST driver. As the German magazine c’t found out it may increase your system’s idle power consumption.
Instructions
The following instructions worked for me. I am using a Samsung SSD 850 Pro as data drive, so the UEFI requirements do not apply (although I do have the BIOS mode set to UEFI). The computer is a Lenovo W540 laptop.
The main points are:
- Update your RST driver to at least version 13.2.4.1000
- Wipe the disk with diskpart clean
- Use Samsung Magician to switch the Encrypted Drive status to ready to enable
- Reboot
- Initialize and format the drive
- Enable BitLocker
The following sections explain the process in more detail.
Update the RST Driver
I had version 12.8.10.1005 of the RST driver installed and Windows Update would not offer any newer version. A visit to Intel’s Download Center got me 13.2.4.1000.
Before the update Samsung Magician would give me the error Failed to perform the operation on the selected disk and all data security modes would be disabled. After the update that was gone.
Diskpart Clean
The disk needs to be in uninitialized state. Open an elevated command prompt and type (this deletes all data on your second hard disk!):
- diskpart
- list disk
- select disk 1
- clean
Samsung Magician
Enable Encrypted Drive status in Samsung’s SSD management software by clicking Ready to enable:
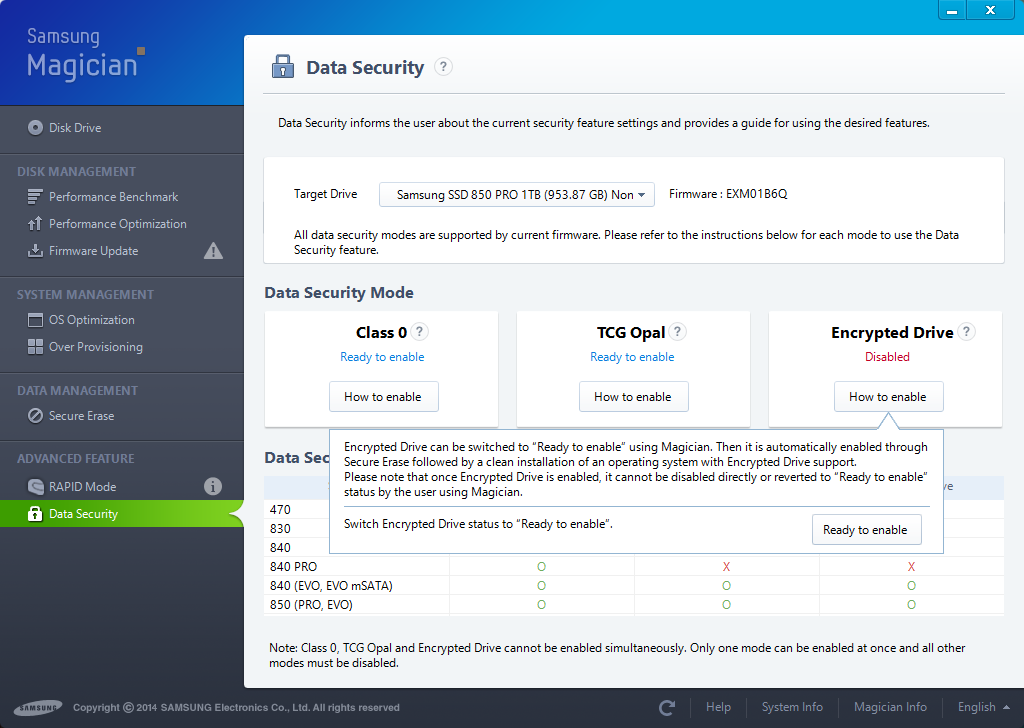
After a reboot it should look like this:
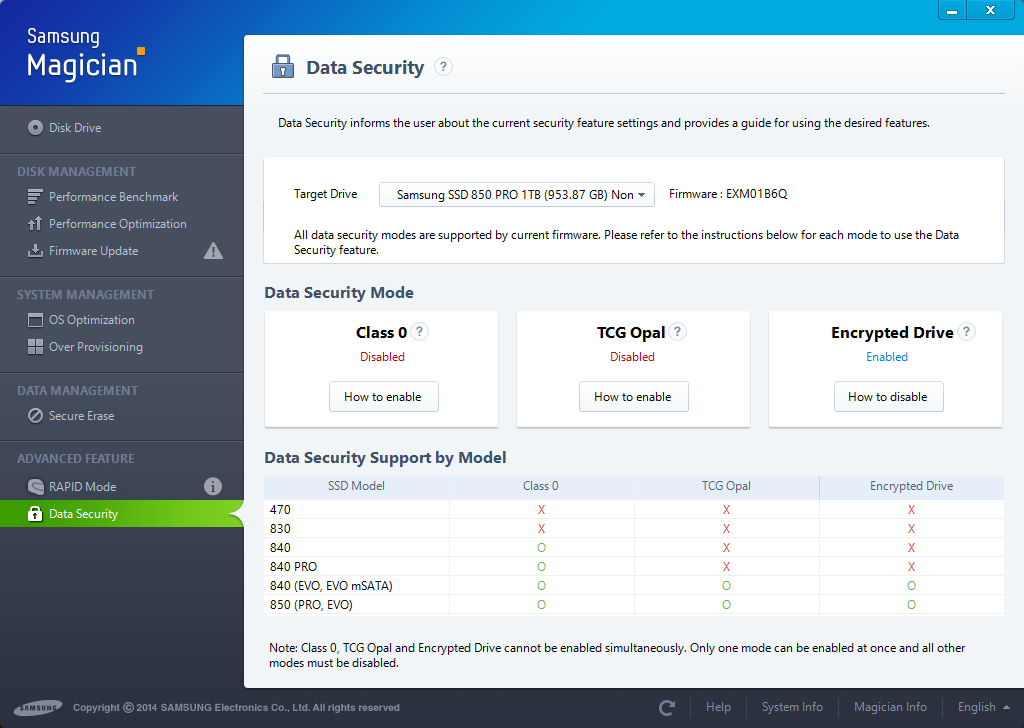
Format the Drive
Initialize and format the drive in Disk Management. Remember: before you do that the drive should be in uninitialized state like this:
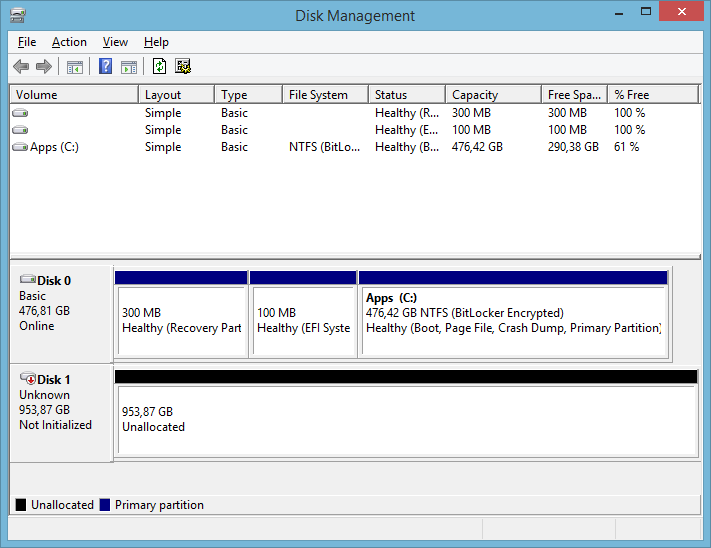
Enable BitLocker
Enable BitLocker the usual way. Make sure you do not get the following screen asking how much of the drive to encrypt, otherwise BitLocker is encrypting in software:
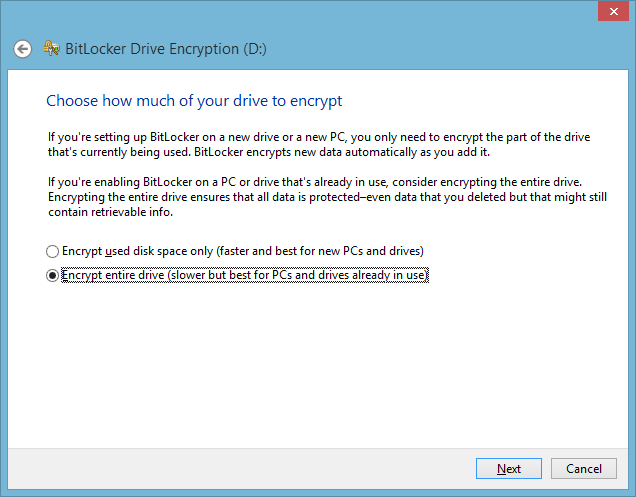
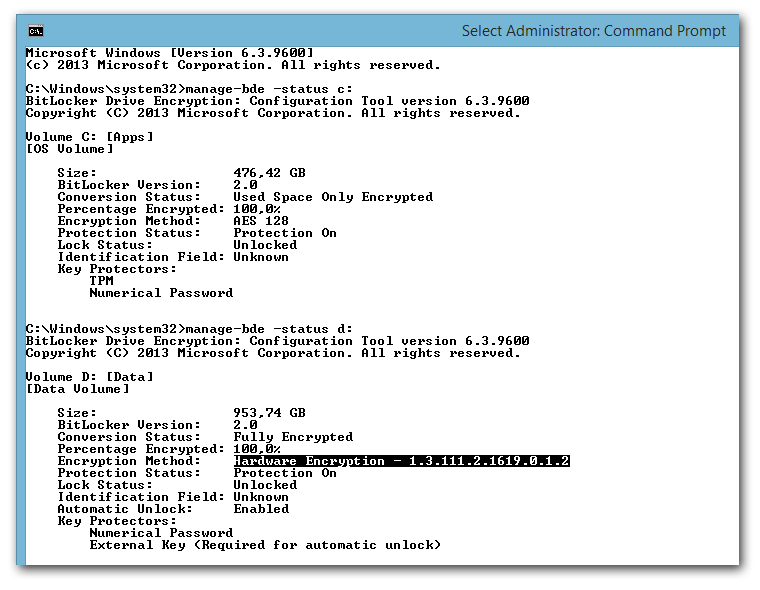
Check if BitLocker really uses Hardware Encryption
The BitLocker UI in Control Panel does not tell you whether hardware encryption is used, but the command line tool manage-bde.exe does when invoked with the parameter status. You can see that hardware encryption is enabled for D: (Samsung SSD 850 Pro) but not for C: (Samsung SSD 840 Pro without support for hardware encryption):





32 Comments
Thank you very much for your guide it told me exactly what I needed to know and I was able to enable hardware encryption on a new secondary drive with out re installing windows.
How can I boot to my DVD drive when CSM is disabled? The option to boot to the drive, and therefore to install Windows, won’t seem to appear for my gigabyte motherboard.
Ok, I figured out the CSM part. I just needed to use rufus to create a bootable usb key.
However, I’m still having a lot of trouble getting this to work. I have a TPM module installed, CSM disabled and UEFI bios use confirmed. I’ve followed the steps exactly for my Evo840 with Samsung Magician, and Gigabyte’s support staff assures me that the motherboard does support edrive. However, every time I get to the step of enabling encryption I get the “Encrypt part of drive or whole drive” question indicating software-based encryption.
As a test, I installed Windows 8.1 to an old SATA drive instead and then activated bitlocker on the Samsung SSD as a secondary drive. That worked great, and when I run the command “manage-bde.exe -status f:” it confirms that the ssd is indeed hardware encrypted in this secondary drive position.
How come I can’t get it working when the SSD is the primary drive? Any ideas would be appreciated!
Hello Helge Klein,
I have tried many, many ways of replicate this post in my Samsung SSD 850 EVO (no PRO) without success. My laptop is an HP without TPM support, and every try I do, leads to software encryption. It is very stressing not to be able to perform the hardware encryption.
I am starting to assume that hardware encryption is available on the PRO version and not* the EVO. Do you know something about this?
Thanks,
Mark.
Also, I forgot to mention that my attemps involve trying to hardware-encrypt the SSD of the OS (not data drive), so I am not sure if the “uninitialized state” applies also to the cases where I want hardware encryption on the OS drive. Any hints will be very welcomed.
To Mark: According to the Samsung Tooltip, to get hardware encryption of an OS drive, you have to install a NEW Operating System on it.
Basically, the steps required would be:
1. Plug the OS drive into A DIFFERENT MACHINE (or the same machine if you’re planning to wipe it, but you can’t boot off of the drive yet…)
2. Do the DISKPART cleaning of the SSD.
3. Run Samsung Magician and “Secure Erase” the drive.
4. Change the drive to “Ready to Enable”.
5. Shut down the computer and install the new OS to the drive.
6. After OS comes up, enable BitLocker on the SSD.
7. Done!
Great article. A good think to note: On my T440P I used to install the latest and greatest rst driver 14.5.0.1081 however after 4 hours of troubleshooting I realized that somehow FDE will not work with this version and will fallback to software (leaving the M$ one works). Not sure what would happen if I add 14.5 after encrypting ran out of patience.
Update: At least on windows 10, installing rst drives will fallback to software encryption, encrypting and then updating the driver for ahci will also break encryption, very difficult to recover via psid revert.
Microsoft changed something on build 10586 aka 1511, and enabling hardware encryption via BitLocker no longer works at least on Samsung SSDs (‘parameter is incorrect’). If you encrypt it on build 10240 and then upgrade to 10586 it will still be enabled, but if you disable it you won’t be able to re-enable it.
Well, those technically inclined can also use MSED, an open-source program to enable SSD hardware encryption.
http://www.r0m30.com/msed
Maybe a dumb question: If i do this with a brand new Evo 850, by hooking it up to my current Windows and perform the steps above. Can i then turnoff the PC, disconnect all the other Harddrives (only leaving the encrypted Evo 850 connected) and install Windows 10 with a clean install?
Or how does this works? I want a hardware-accelerated completely encrypted Evo 850 with Windows 10 clean installed.
Did you try? I am wondering if that will work too. I have a SAM SUNG 850 Pro with hardware encryption and I want hardware encryption on my C: drive. Basically this is my setup:
– ThinkPad T520 with 2 disk drives
– SSD is connected to the SATA controller, it’s my primary drive (850 Pro)
– HDD is connected in place of the optical drive through a disk caddy
– My computer is old but it’s UEFI capable
This is what I did:
– Created a brand new Windows 10 boot media (using a USB stick)
– Booted on Windows 10 using this USB and clicked on “Repair your computer”
– Opened up CMD and started disk part
– I zeroed both disks using “clean all” option (this turns them back into MBR)
– Converted them back into GPT with convert gpt
– Installed Windows 10 on the secondary disk drive, not the SSD
– Installed SAMSUNG Magician and it automatically detected my SSD drive as “Encrypted”
I still didn’t format the SSD drive as I ran out of time last night.
I will perform a few tests tonight with the secure erase and see what I get.
I’ve been trying to figure out the hardware encryption on my 850 Pro for a while and I had a lot of problems creating that bootable usb drive using Samsung Magician. There’s no way that I could have gone past an error message saying that the media creation failed. I performed all sorts of research and I finally found this GREAT article which actually explains how to do this. Thank you, author !
I will paste the rest of my tests here after I get home.
I van make a backup from the hardware Bitlocker encrypted drive using Acronis True image 2016. But I have not managed to restore a backup.
How can that be done?
Has anyone figured out how to restore a system image backup to a hardware encrypting SSD (eDrive)? The problem I am experiencing is that I can successfully restore the system image to the SSD but hardware encryption is no longer enableable like it was before the backup and restore.
I have written-up the full test procedure here: http://answers.microsoft.com/en-us/windows/forum/windows_10-update/how-to-restore-a-system-image-backup-to-a-hardware/c4140eed-0323-4134-befb-c10335790b64
This weekend I did some more testing using a new self-encrypting solid state drive, a Crucial MX300, which supports Microsoft’s eDrive standard.
What I learned is that restoring a Microsoft system image backup from the M500 breaks the hardware encryption capability but otherwise works normally. I also tried cloning the M500 to the MX300 using Paragon Hard Disk Manager but that broke the hardware encryption capability as well. And lastly, I tried imaging and then restoring the M500 to the MX300 using Paragon HDM but got the same results: Windows works fine but the hardware encryption is not re-enableable.
So the conclusion from all of these tests seems to be that if your eDrive fails, or if you want to migrate to a new eDrive, you will have to reinstall Windows and all of your programs from scratch.
I wish that some Microsoft engineers working in the Bitlocker department would address this shortcoming by either explaining why this behaviour exists (maybe they think it is necessary for security reasons) or treating it as a bug and working on fixing it.
I can’t believe that no one else has raised this issue already! To me it seems like as a major problem with the whole self-encrypting eDrive architecture. You should be able to replace a drive without the hardware encryption breaking and your system image backups becoming useless.
Storage type must be ACHI
The computer must always boot natively from UEFI.
The computer must have the Compatibility Support Module (CSM) disabled in UEFI.
The computer must be UEFI 2.3.1 based and have the EFI_STORAGE_SECURITY_COMMAND_PROTOCOL defined. (This protocol is used to allow programs running in the EFI boot services environment to send security protocol commands to the drive).
TPM chip is optional
Secure boot is optional
GPT and MBR are both supported
if there is RST software/drivers it has to be at least version 13.2.4.1000
this can be done with 2 disks or one
From a windows install that meets the above criteria
set state to ready to enable via Samsung Magician
Make a secure erase USB (for dos)
Reboot pc, change boot mode to bios boot (for the secure erase USB)
boot into secure erase, erase
Reboot pc, change bios boot settings to EFI again (do not let the pc start booting from the drive or you might start the process from beginning)
boot back to windows disk and check via Samsung magician or install windows to your secure erased disk
This is incorrect. For Hardware Encryption, the TPM is absolutely required. You cannot have a hardware bitlocker accelerated drive without a TPM enabled and CSM disabled. You must have the drive set to hardware accelerated mode (active). Also, you cannot secure erase a Samsung drive set to hardware accelerated active mode. This too is incorrect. You must secure erase the drive before setting the drive to hardware accelerated mode.
Hello,
Thank you for the useful article!
I have a Samsung 850 Pro and would like to implement full disk hardware encryption on a dual-boot machine with Debian and Windows 8.1.
The hardware is a Thinkpad T440p.
Could you please advise me whether setting up BitLocker from within Windows would enable me to use the SSD for booting Debian?
Which would be the best approach in such a scenario?
As far as I understand, MSED does not enable suspend to RAM (sleep). Hence, I would prefer to avoid it.
Thank you!
Kind regards,
Nikolay
Hello
Thanks, I’ve managed to encrypt Samsun 850 Evo using this method.
Did anyone test Samsung 960 EVO M2 for hardware encryption?
Please let me know
Thanks
NCM
Yes, it works with the newest firmware. But there is a general problem which makes it impossible to use Bitlocker Hardware encryption when the drive is used as the system drive
See here for more details
https://us.community.samsung.com/t5/Memory-Storage/HOW-TO-MANAGE-ENCRYPTION-OF-960-PRO/m-p/319199/highlight/true#M2354
Yes, the Samsung 960s can use hardware accelerated edrive encryption for both system or data drives in Windows 10 and 11. Tested and working.
Shame it turns out SSD hardware encryption is easily bypassed. https://www.theregister.co.uk/2018/11/05/busted_ssd_encryption/
Better go back to enforcing software encryption on your ssd again.
Unfortunately, I wasn’t able to get it to work on my machine with 970 EVO Plus NVMe drive (Z390 Aorus Master motherboard with TPM). Over 4 hours, trying everything here and everywhere else that I could find on the net.
Thank you for the instructions. I tried to get it to work using my Samsung 980 PRO M.2 SSD.
Question:
This is the only drive in my system. (I have a Dell XPS system)
Magician only works under Windows.
So if I wipe my drive clean I cannot start Magician, to enable hardware encryption.
I’ve tried enabling hardware encryption **before** wiping the disk clean, but this did not work.
Has anybody found a workaround for this probem?
(After re-installing Windows four times in a row I’m ready to give up)
You would have to pull the drive and put it into another system. Secure erase the drive and then set the drive to hardware acceleration active. Reinstall the “empty” drive back into the original system. Install the OS as usual. Change the group policy to force hardware acceleration. Enable bitlocker.
You need to pull the drive and put it into a different Win1x Pro machine as a fixed drive. Use the Samsung software to secure erase the drive. Reboot into Win 1x Pro and run Magician 7.x. Enable hardware acceleration. Remove drive and put back into the XPS computer. Install the OS. Edit the local group policy to force hardware acceleration. Enable bitlocker. Save your recovery keys!! You will need them if you update the bios.
I have a Lenovo IdeaPad with Samsung SSD (960 Pro M.2) only for 4 months. It unexpectedly gave a blank screen. On re-boot, it displayed “BitLocker Recovery” and the “Recovery Key for this drive” (32-bits key), and stated that BitLocker needs your recovery key to unlock your drive because security boot has been disabled. I found the Microsoft info on “BitLocker recovery: known issues” It explained what is the 32-bits key. And under “Tablet devices do not support using Manage-bde…”, it shows the “Workaround” for the steps Troubleshoot > Advanced Options > Command Prompt.
(1) Would this workaround also works for the Lenovo IdeaPad?
(2) The screen instruction shows “Use numeric key or F1-10 to enter the 32-bits key. But I cannot enter any letters in the key.
I need help! The data on the SSD is critical. I cannot wipe the SSD.
Pull the drive and put it into another Win 1x Pro machine. Enter the recovery key when prompted.
Your “Recovery Key” is only composed of numbers. It is not the same as your Bitlocker password which you can define whatever combination of numbers and letters etc. yourself. You always and easily change your Bitlocker password, but the recovery key is permanent until you turn it off. If you have a Microsoft logon, Microsoft stores the key for you, otherwise you would have had to save, print or store the key elsewhere when you enabled Bitlocker drive encryption.
Thank you for this guide Helge!
Although I carefully followed the steps I was unable to get any hardware encryption on my Samsung 870 EVO SSD.
It turns out, if you’re using a Windows Pro edition, you should also check the Group Policies.
1. Open the Local Group Policy Editor
2. Navigate to this folder:
Computer configuration -> Administrative Templates -> Windows Components -> Bitlocker Drive Encryption
3. Check at the following settings depending on your requirement:
– Fixed Data Drives -> Configure use of hardware-based encryption for fixed data drives (Should be ‘Enabled’)
– Operating System Drives -> Configure use of hardware-based encryption for operating system drives (Should be ‘Enabled’)
4. For drives not supporting hardware encryption, you can also configure Bitlocker to use a stronger encryption then default used (AES-128) with this setting:
– Choose drive encryption method and cipher strength ()
“…it means that you cannot clone a drive with data on it and enable BitLocker with hardware encryption afterwards.”
This is absolutely incorrect. You can clone a drive and have IEEE-1667 activated on the new drive. Upgraded many SSDs from smaller to larger drives AND activated hardware-accelerated Bitlocker. There are a couple of extra steps, but you can totally change SSDs and take your drive image with you to the other drive.
Could you kindly explain the extra steps needed to clone an SSD this way?