Upgrading Ubuntu 14.04 to 16.04 & PHP 5.6 to 7 for WordPress
- Website
- Published Feb 22, 2017 Updated Dec 31, 2019
This post describes how I upgraded our webserver running WordPress on Apache from Ubuntu 14.04.5 LTS to 16.04.1 LTS. Please see this article for more information on the server’s installation and configuration.
Backup
Backup your machine by exporting the VM from Hyper-V Manager.
Note: to be on the safe side I ran all following commands on the console, not via SSH.
Install all available updates
sudo apt-get update
sudo apt-get dist-upgrade
sudo apt-get autoremove
Reboot and check Apache’s error log:
sudo shutdown -r now
tail /var/log/apache2/error.log
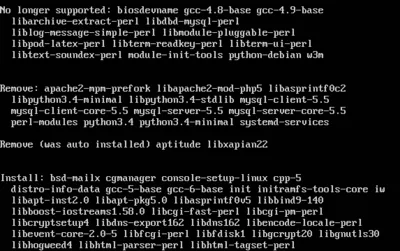
Upgrade to Ubuntu 16.04.1
sudo do-release-upgrade
During the upgrade process:
- When asked whether to install the updated version of security.conf, select “yes”
- When asked whether to install the updated version of /etc/logrotate.d/apache2, select “yes”
Migrate from PHP 5.6 to PHP 7
Remove PHP5
sudo apt-get purge php5-common
sudo apt-get autoremove
sudo apt-get install libapache2-mod-php
Install missing PHP7 modules
sudo apt-get install php7.0-mysql php7.0-curl php7.0-gd php7.0-json php7.0-mbstring php7.0-mcrypt php7.0-opcache php7.0-tidy php7.0-xml php7.0-xmlrpc
sudo service apache2 restart
Apache Configuration
Enable the mod_ext_filter Apache module for W3 Total Cache:
sudo a2enmod ext_filter
sudo service apache2 restart
Security.conf
Edit /etc/apache2/conf-enabled/security.conf to send only minimal information about the server:
ServerTokens Prod
ServerSignature Off
TraceEnable Off
Add the following to your Apache configuration file /etc/apache2/conf-enabled/security.conf:
# Prevent MSIE from interpreting files as something else than declared by the content type in the HTTP headers.
# Requires mod_headers to be enabled.
Header set X-Content-Type-Options: "nosniff"
# Prevent other sites from embedding pages from this site as frames. This defends against clickjacking attacks.
# Requires mod_headers to be enabled.
Header set X-Frame-Options: "sameorigin"
# Block pages from loading when they detect reflected XSS attacks
# Requires mod_headers to be enabled.
Header set X-XSS-Protection: "1; mode=block"
# Pre-existing site uses too much inline code to fix, but wants to ensure resources are loaded only over https
# Requires mod_headers to be enabled.
Header set Content-Security-Policy: "default-src https:; font-src https: data:; img-src https: data: 'self' about:; script-src 'unsafe-inline' 'unsafe-eval' https: data:; style-src 'unsafe-inline' https:;"
# Only connect to this site and subdomains via HTTPS for the next year and also include in the preload list
# Requires mod_headers to be enabled.
Header set Strict-Transport-Security: "max-age=31536000; includeSubDomains; preload"
Restart Apache:
sudo service apache2 restart
Adjust the Logrotate Configuration
Edit /etc/logrotate.d/apache2 so that it says:
rotate 30
dateext
PHP Hardening and Optimization
Add the following to disable_functions in /etc/php/7.0/apache2/php.ini: exec,system,shell_exec,passthrough
Configure PHP’s opcache via etc/php/7.0/apache2/php.ini:
opcache.enable=1
opcache.memory_consumption=256
opcache.interned_strings_buffer=10
opcache.max_accelerated_files=10000
Restart Apache:
sudo service apache2 restart
Re-enable the mod_pagespeed Repository
This was disabled during the upgrade.
sudo rm /etc/apt/sources.list.d/mod-pagespeed.list
sudo mv /etc/apt/sources.list.d/mod-pagespeed.list.distUpgrade /etc/apt/sources.list.d/mod-pagespeed.list
Check for errors
Check Apache’s error log:
tail /var/log/apache2/error.log





Comments