Access Denied Trying to Connect to Administrative Shares C$, D$ etc.
Under certain circumstances, you cannot connect to administrative shares (e.g. C$) on remote computers, even though you use the right credentials. Accessing a normal (i.e. non-administrative) share works flawlessly, though.
Problem
In this situation you get the following error when trying to connect to the admin share in Explorer:
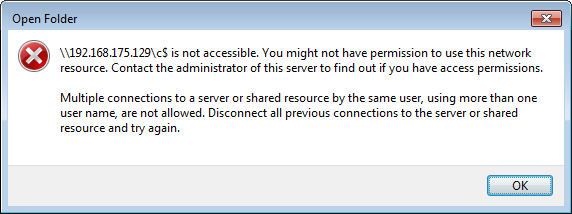
This is the message text:
\\192.168.175.129\c$ is not accessible. You might not have permission to use this network resource. Contact the administrator of this server to find out if you have access permissions.
Multiple connections to a server or shared resource by the same user, using more than one username, are not allowed. Disconnect all previous connections to the server or shared resource and try again.
The message hints at multiple connections, but that is misleading.
When you try to connect to the admin share on the command line, you get a different error message:
C:\>net use \\192.168.175.129\c$ /user:win7-2\admin *
Type the password for \\192.168.175.129\c$:
System error 5 has occurred.
Access is denied.
Solution
As described in MS KB article 951916, Microsoft introduced as part of UAC a little known feature called “UAC remote restrictions”. It filters the access token for connections made with local user accounts or Microsoft accounts (the latter typically have the format MicrosoftAccount\EMailAddress). In other words, it removes the SID for “Administrators”. Connections made with domain accounts remain unchanged.
From KB951016:
If the user wants to administer the workstation with a Security Account Manager (SAM) account, the user must interactively log on to the computer that is to be administered with Remote Assistance or Remote Desktop, if these services are available.
LocalAccountTokenFilterPolicy
One may like this or not, the solution is luckily pretty simple. UAC remote restrictions can be disabled by setting the registry value LocalAccountTokenFilterPolicy to 1:
Key: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System
Value: LocalAccountTokenFilterPolicy
Data: 1 (to disable, 0 enables filtering)
Type: REG_DWORD (32-bit)
Setting LocalAccountTokenFilterPolicy From the Command Line
The above value can be set with the following command:
reg add HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System /v LocalAccountTokenFilterPolicy /t REG_DWORD /d 1 /f
After a reboot access tokens from remote connections are not filtered any more. On Windows 8 and Windows 10, the reboot is not even required any more.




37 Comments
I am assuming the UAC reg key is not the case if one admin account (set on both machines) will access the C$ with ease but a newly created admin account on both local and server will toss the access denied prompt. Starting to bug me now and I will probably figure it out come the time anyone responds, but have narrowed it down to a server side error as the local account on the client machine will utilize network level auth to pull remote system info on another machine, but will get the access denied when trying to save that file on the server.
I use a mechanism that runs net use command to verify the local admin account password has not changed on my windows 2003 servers. When we upgraded to 2008 it broke with the system error 5 message. Found your post and this worked for me. Thanks
Big thanks on this article, I found it very useful. I was about to make some backups from my laptop to my desktop, and have just been struggling for more than half an hour with connecting. I was just about to give up when realized that I (for some strange reason) have left the wicked UAC feature enabled on the laptop, so that this could have something to do with it. A Google search “uac admin shares” took me here, and a couple of minutes later I was fixed. In my case, the Windoze registry didn’t even have a DWORD there, so at first I thought I was in the wrong key folder. Anyways, I created the DWORD and rebooted the system. Everything worked. Big thanks!
Thanks for the workout … it really work as champ. I was havning problem while access c$ of window 2012 using local admin accout. This regitry twik works and aslo as mention reboot not required.
Great find. Thanks much for the tip!
Very usefull!!! Thanks much
great tip. worked for me on srv 08. did not even have the Dword, had to add it. srv is a workgroup in dmz
super! was struggling with this for backing up my servers with veeam in dmz…
added the key in 2012R2 and it work perfect now!!
guys, This did not work for me in windows server 2008 r2. Please help
To avoid a reboot, simply restart the “Server” Service (along with Computer Browser) in services.msc
The correct KB article is: 951016
Thank you, you saved me hours of hair pulling.
great!!!!
I had the problem for two years. Thanks
I’m having the same issue – ran the regedit and rebooted but this hasn’t worked for me either – anyone got any other suggestions?
Struggled with this issue since Windows 7. Is still the same in latest Windows 10 release (Creators Update, Version 1703, Build 15063).
Used the fix as described, – works perfectly.
Super ! Thank you.
Worked like a charm. I do nothave a domain but a standalone Windows 2012 server, and with this solution I was able to map administrative shares with a user account with administrative rights.
Thanks, that worked on Win 2008 R2 which was not on a domain
It is strange. when I add the key and set to 1. It could work right after the server reboot, but about half an hour passed, the error will appear gain.
Could any one help? thanks a lot!
Right click Computer and hit Manage
Under System Tools, double click Local Users and Groups then click Groups
Right click Administrators
Click Add to group then click Add then Advanced
Click Find Now
Double click on Local Service then click OK
NT Authority\Local Service should show up in the list, click OK then Reboot
I wanted access to backup files remotely on a Windows 10 pro home group.. This worked fine. I created a .reg file that saved me time and will also create the registry entry as well, if it is missing as it appears to be on Windows 10 Pro.
A .reg file is is just a text file with a .reg extension. create a text file and save it as EnableRemoteHiddenShares.REG then you can just right click on it and use the merge option. or just double click on it.
—-
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrentVersionPoliciesSystem]
“LocalAccountTokenFilterPolicy”=dword:1
—-
Thank you so much.
It worked great in W7 Pro. Actually it solved a lot of issues which needs admin privileges for local users.
The key was not there, so I just created and it worked.
Wow… six years later and this is *still* so relevant. Excellent work Helge. There is an awful lot of mis-information on the ‘net about this issue and how to fix it. Well done.
This did not work for me on Windows 7 32 bit machine.
I used this solution everytime… but for some pc, with windows 10 pro, i don’t know why (I think after some windows update) this solution is not enough. Pc (server side) asks me username and password, but does not recognize them. I tried disabling antivirus and firewall, but nothing to do.
Try this work around; share the network folder (i.e. \\server\C) and grant the user (i.e. user1) read access+.
Now test and see if it works. This should also bypass UAC Remote Restrictions as you explicitly shared the network share.
If it still fails, setup the same user on your local computer and try again.
Access Denied Trying to Connect to Administrative Shares C$, D$ etc.
Open Registry -regedit
run as administrator
Then copy paste below link to the registry
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System
create new – Dword (32bit value)
LocalAccountTokenFilterPolicy
Value data change-1
Thank you!!!
We have 3 Win 2008 R2 servers (plus some 2012s). I can access admin shares (C$, D$) at will out of the box with all of them except one 2008 R2 box. I get the same message as posted above. I’ve tried both the domain administrator account and the local administrator account.
I compared the registry on all 3 2008 boxes and they are all exactly the same – none of them have that key. Two of them I can access fine, the other one I can’t. Firewalls are off on all of them.
I also checked the local administrators group for the LOCAL SYSTEM account and it is not there in all 3 boxes.
I know this is an old post but maybe somebody has new info.
Thanks.
Had an issue with Veeam B&R using a local account for connecting and activating VSS, applied this solution and worked for me. Great! Thanks
Thank you so much!!! Making this change allowed me to access the admin shares.
This Worked for me as well, Thanks!
8 1/2 years later and this helped me out on Windows Server 2016, thank you!
I thought this was a local security policy to adjust but I could not find it. This fix resolved it and yes with no reboot required. By the way, it seem to also have unlocked ability to shutdown remotely (shutdown -m \\computername) this was also not possible until applying this fix (no reboot neither)
Thanks for the solution.
Awesome Blog… it worked for me on Windows 2016 Std Server. I was trying to manage the server on WMI and failing to even get the admin share remotely of the servers running in workgorup… implement the reg key and restarted, all good.
Thank you.
LocalAccountTokenFilterPolicy – wasn’t there.. Added this key with value 1..
It works in Windows 10 Pro 64 Bit..
Thanks for the tip.
Great find! Thanks so much.
Such frustration. One of my home servers stopped accepting access to admin shares via UNC from any other machine on the network. Same credentials for admin accounts but this thing wouldn’t go.
Reg added and immediately works.
Thanks heaps!
Spent 5 hours working on this. Your link saved me no telling how many more. Thanks!