How to Check the TPM Status & Enable the CPU’s fTPM/PTT
The recent Windows 11 announcement has created a lot of confusion due to the requirement for a trusted platform module (TPM). This article explains why your machine almost certainly has a TPM, how to check the TPM status and how to enable the TPM that comes with your CPU.
Why Your Machine (Almost Certainly) Has a TPM
Windows 10 TPM Requirement for OEMs
If you bought your machine with Windows 10 in the past five years, it has a TPM: all new or updated devices must come with an enabled TPM 2.0 as of July 28, 2016, as stated in the Windows 10 minimum hardware requirements. This applies to all desktop versions of Windows 10 (Home, Pro, Enterprise, and Education).
CPU-Based TPM: Intel PTT & AMD fTPM
If you have a custom-built PC or a machine that was sold without Windows 10, chances are excellent that your CPU has an embedded TPM. Ever since Skylake (6th gen), nearly all Intel CPUs have an embedded TPM 2.0 that Intel calls Platform Trust Technology (PTT). AMD CPUs have an embedded TPM 2.0 called fTPM since the AM4 platform (2016).
- List of Intel CPUs officially supported by Windows 11
- List of AMD CPUs officially supported by Windows 11
Check Your Machine’s TPM Status
There are many different ways you can check if your machine has an enabled TPM.
Settings App
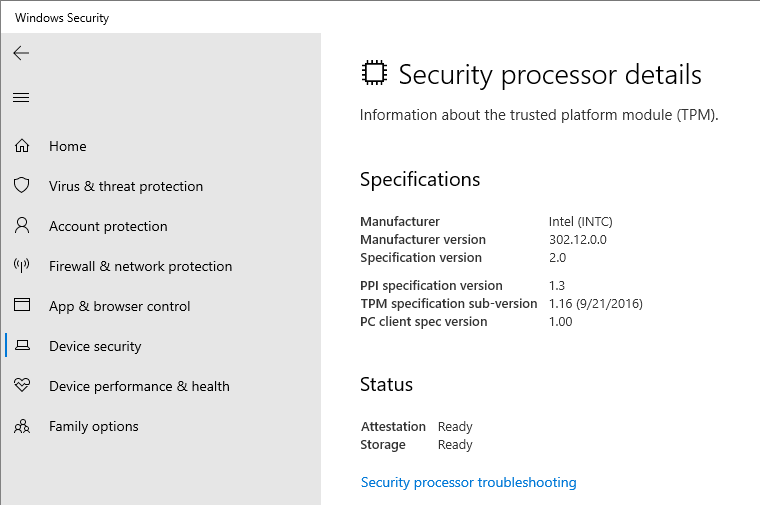
Open the Settings UWP app on the Device security tab by opening the URI windowsdefender://devicesecurity. If a TPM is enabled, you’ll see a link to the Security processor details page which looks as follows for an Intel PTT:
Management Console (MMC)
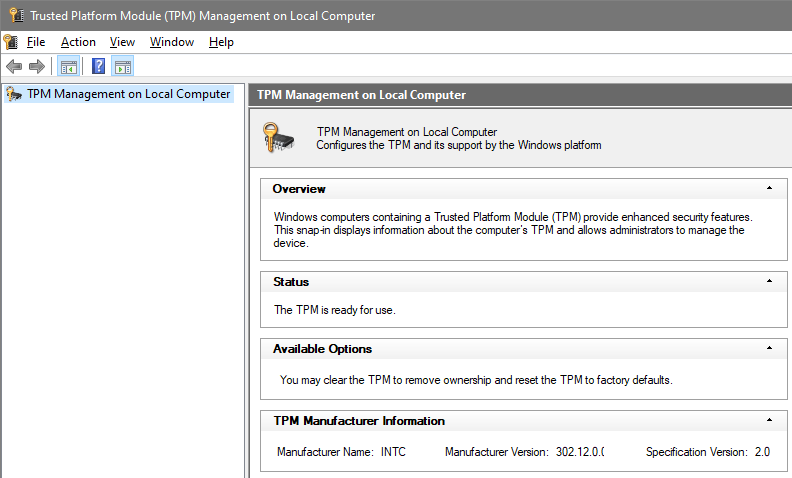
Open the Windows MMC snap-in tpm.msc. If your machine’s TPM is enabled it should look similar to the following:
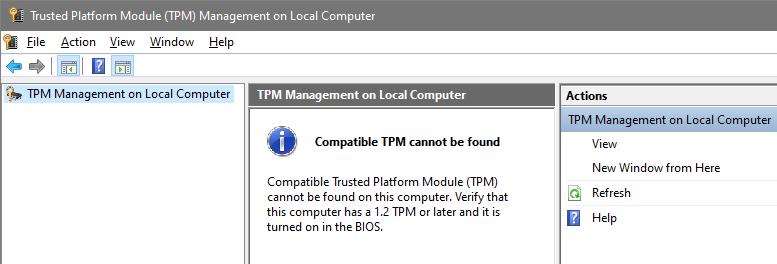
If the TPM is disabled, on the other hand, the MMC looks like this:
Command-Line Tool
The Windows command-line tool tpmtool shows detailed status info when called with the parameter getdeviceinformation. This does not require elevated permissions. Here’s the output from a machine with the Intel PTT:
C:\>tpmtool.exe getdeviceinformation
-TPM Present: True
-TPM Version: 2.0
-TPM Manufacturer ID: INTC
-TPM Manufacturer Full Name: Intel
-TPM Manufacturer Version: 302.12.0.0
-PPI Version: 1.3
-Is Initialized: True
-Ready For Storage: True
-Ready For Attestation: True
-Is Capable For Attestation: True
-Clear Needed To Recover: False
-Clear Possible: True
-TPM Has Vulnerable Firmware: False
-PCR7 Binding State: 0
-Maintenance Task Complete: True
-TPM Spec Version: 1.16
-TPM Errata Date: Wednesday, September 21, 2016
-PC Client Version: 1.00
-Is Locked Out: False
PowerShell
The PowerShell cmdlet Get-Tpm needs to be run with elevated privileges. Its output looks as follows for an Intel PTT:
PS C:\> Get-Tpm
TpmPresent : True
TpmReady : True
TpmEnabled : True
TpmActivated : True
TpmOwned : True
RestartPending : True
ManufacturerId : 1229870147
ManufacturerIdTxt : INTC
ManufacturerVersion : 302.12.0.0
ManufacturerVersionFull20 : 302.12.0.0
ManagedAuthLevel : Full
OwnerAuth : MA9JHWcXmATuXijf7kwOSsCCCxU=
OwnerClearDisabled : False
AutoProvisioning : Enabled
LockedOut : False
LockoutHealTime : 10 minutes
LockoutCount : 0
LockoutMax : 31
SelfTest : {}
As you can see above, the TPM version (1.2 or 2.0) is not available via the Get-Tpm cmdlet.
WMI
The WMI class Win32_Tpm needs to be queried with elevated privileges. In PowerShell this looks as follows for an Intel PTT:
PS C:\> Get-WmiObject -Namespace "Root\CIMV2\Security\MicrosoftTpm" -query "Select * from Win32_Tpm"
__GENUS : 2
__CLASS : Win32_Tpm
__SUPERCLASS :
__DYNASTY : Win32_Tpm
__RELPATH : Win32_Tpm=@
__PROPERTY_COUNT : 10
__DERIVATION : {}
__SERVER : HK87K
__NAMESPACE : Root\CIMV2\Security\MicrosoftTpm
__PATH : \\HK87K\Root\CIMV2\Security\MicrosoftTpm:Win32_Tpm=@
IsActivated_InitialValue : True
IsEnabled_InitialValue : True
IsOwned_InitialValue : True
ManufacturerId : 1229870147
ManufacturerIdTxt : INTC
ManufacturerVersion : 302.12.0.0
ManufacturerVersionFull20 : 302.12.0.0
ManufacturerVersionInfo : Intel
PhysicalPresenceVersionInfo : 1.3
SpecVersion : 2.0, 0, 1.16
PSComputerName : COMPUTERNAME
Please note the format of the SpecVersion field: major specification version, minor specification version, specification revision. If you’re looking for the TPM version, you’re probably only interested in the major version (2.0 or 1.2).
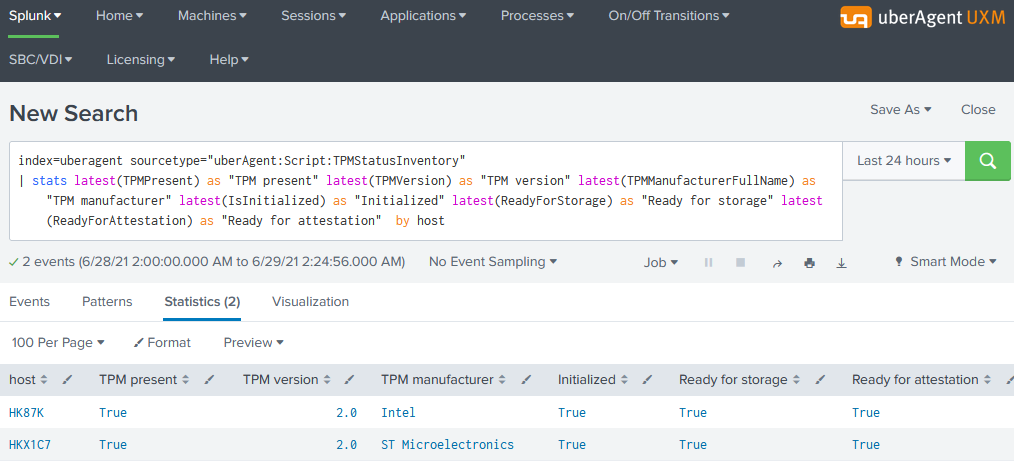
uberAgent (TPM Status Inventory)
As an enterprise, you need an inventory of your devices’ TPM status. Take a look at this uberAgent practice guide which explains how to collect regular TPM status from any number of endpoints. The results are stored in Splunk for easy analysis and reporting:
Enable the CPU’s fTPM/PTT
To enable your CPU’s built-in TPM boot into the UEFI settings (what used to be the BIOS setup), localize the setting often simply called fTPM (AMD CPUs) or PTT (Intel CPUs), and enable it.
Caveats
- Some mainboards might be lacking this BIOS setting to enable the CPU’s TPM. In that case, your only hope is a BIOS update.
- TPM 2.0 is only supported in UEFI mode, not in legacy BIOS mode. Switching from BIOS to UEFI mode may prevent an installed OS from booting.
More Information on TPMs
What Is a TPM?
A TPM can calculate random numbers, RSA keys, decrypt short data, and store hashes taken when booting the device. A TPM incorporates in a single component:
- A RSA 2048-bit key generator
- A random number generator
- Nonvolatile memory for storing EK, SRK, and AIK keys
- A cryptographic engine to encrypt, decrypt, and sign
- Volatile memory for storing the PCRs and RSA keys
TPM 1.2 vs. TPM 2.0
The newer TPM 2.0 standard offers security advantages over TPM 1.2, which is limited to the RSA and SHA-1 hashing algorithms.
TPM 1.2 parts are available as discrete silicon components (dTPM) only, whereas TPM 2.0 can also be integrated as firmware-based components (fTPM), e.g., into CPUs.
TPM Initialization
Starting with Windows 10, the OS automatically initializes the TPM. This is a change from earlier Windows versions, where you would initialize the TPM and create an owner password.
Windows Features That Require a TPM
The following Windows features require TPM support (source):
| Windows feature | TPM version |
|---|---|
| Measured Boot | TPM 1.2 or 2.0 |
| Device Encryption | TPM 2.0 |
| Windows Defender System Guard | TPM 2.0 |
| Device Health Attestation | TPM 1.2 or 2.0 |
| Virtual Smart Card | TPM 1.2 or 2.0 |
| Autopilot | TPM 2.0 |
| SecureBIO | TPM 2.0 |
| DRTM | TPM 2.0 |





13 Comments
The Article states that all Intel Chips since then have PTT but in fact non of the K Series Intel CPUs have this until 8th Gen. Only non K varients of 6th and 7th Gen have PTT
You can check this via Intel ARK.
Due to the fact that most DIY builder use K Series CPUs this is very important.
Sir, you might be comparing trusted execution tech with ptt. I have enabled ptt in 6700k in msi z170 board since long maybe around 2019, for my own research for bitlocker.
But MS might be restricting the processor due to txt tech and thats entirely possible. Nevertheless for now i have tpm 2.0 for my work, i will change hardware before 2025.
No one mentions that discreet TPM is the most secure and it’s a hardware solution unlike the others which are software solutions and less secure
Any sources for that claim?
If it’s embedded on the CPU chip, it means it’s hardware based as well.
Not exactly, the cpu based ptt is just emulator so the OS can think the system has tpm 2.0
The actual chip has ic for storing keys and certificate data, and softwares other than os cannot reach hard tpm, whereas cpu memory vulnerability and ultra delux prowess of emulated hardware is well known.
That url merely opens a bing search page.
Which URL?
thanks
Good article and explanation of TPM. The title may be a bit misleading though as there are *many* systems out there without TPM or PPI.
Those who game or do other intensive work upgrade their hardware fairly regularly, but those that just browse the web, email, watch youtube, and occasionally use office apps get along fine on old hardware. My wife is running an i3 gen 1 system and has no complaints. I’ve offered a few times to upgrade her to something newer, she says it’s fine as is. Other relatives are running gen 3 and 4 systems without issue. These old systems serve up Win 10 just fine for casual users (as long as they have 8GB memory, even better if they have an SSD). When the time comes where they must upgrade, I’ll help them get small form factor used corporate systems which are relatively inexpensive. I’ve purchased several used corporate machines over the years and had good luck.
THANK YOU!!! I have been reading TPM articles and trying to figure out how my less than one year old gamer machine didn’t have TPM! — PTT! Found it. Thank you for posting this and helping folks that are trying to figure this out!
PowerShell cmdlet Get-Tpm
Why you have? :
RestartPending : True
thank you so much this article is the best thing ever