Azure DevOps: Restricting Credentials to a Single Repository
- Software Development
- Published May 25, 2020
You may find yourself in a situation where you need to limit a set of credentials to a single Git repository only - like I did when I was working on a Git-based configuration backup solution for Linux. In such a case, you want the Git credentials you are storing per machine to grant access to that machine’s repository only. As useful as such a setup is from a security point of view, it is currently difficult to implement in Azure DevOps.
Single Repository Credentials
Unfortunately, there does not seem to be an easy way to generate credentials that are valid only for a single repository in Azure DevOps. I would have expected the ability to limit personal access tokens (PATs) or SSH keys to individual projects, but that functionality is simply missing. Repository access can only be granted on the user level. This means that you have to create a new user in Azure AD (if your DevOps instance is backed by AAD) and give this new user permission on the repository used for the backup only. This also means that you need one user account per repository. Quite inelegant.
Creating the User and Generating the PAT
If you are forced to go down this route follow these steps:
- In Azure DevOps, create a new project.
- Optionally rename the project’s default repository. If you plan to create one repo per machine to backup, it might make sense to name the repositories after the machines.
- In Azure AD, create a new user.
- In Azure DevOps, go to organization settings and add the new user.
- Give them “Contributor” access to the new project only. You do not want this user to be able to access any other projects in your Azure DevOps.
- Log in to Azure DevOps with the new user.
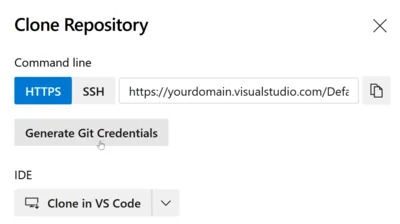
- Navigate to the repo and click Generate Git Credentials to create a personal access token (PAT).
- The PAT can be found in the user settings as
Git: https://yourdomain.visualstudio.com/ on the website.You might want to edit it to change the name to something more meaningful likeBackup COMPUTERNAME
- The PAT can be found in the user settings as
Azure DevOps Git on the Linux Command Line
Accessing the new repository requires authentication with the Git credentials you generated previously. If you want a seamless push/pull experience without having to manually enter the password you can embed the credentials in the remote URL. The format is as follows:
https://PAT_USER:PAT_PASSWORD@REPO_URL
Example
Given the following:
Repository URL: https://yourdomain.visualstudio.com/your_project/_git/your_repo
PAT user: your_username
PAT password: this_is_typically_a_long_random_string
The DevOps PAT URL to use as Git remote is:
https://your_username:this_is_typically_a_long_random_string@yourdomain.visualstudio.com/your_project/_git/your_repo
To store that PAT URL as Git remote URL run the following command:
git remote add origin PAT_URL
PATs That Don’t Work
It took me a while to figure out that the PAT needs to be generated by clicking “Generate Git Credentials”. At first, I tried PATs created on the Personal Access Tokens page on DevOps, accessible through the URL https://yourdomain.visualstudio.com/_usersSettings/tokens. However, no matter what I tried, those PATs always resulted in HTTP status 403 (forbidden). Many others seem to have had similar problems, as documented by this Stack Overflow question. The official documentation is a bit vague on the subject.
What About GitHub?
The whole thing is much easier and more logical on GitHub because it has Deploy Keys, SSH keys that grant access to a single repository only and are perfect for automation. Just what I needed for my machine configuration backup project.





Comments