Simple OPNsense Firewall Rules for a Secure Smart Home
- Home Automation, Networking & Self-Hosting
- Published Dec 13, 2024
This article presents a simple, balanced OPNsense firewall configuration for a secure smart home. The config provides good security while still allowing the freedom that is required by a family that is comprised mostly of people who wouldn’t call themselves IT geeks. This post is part of my series on home automation, networking & self-hosting that shows how to install, configure, and run a home server & network with dockerized or virtualized services.
Principles
Network Segmentation
- We segment the network into VLANs and only allow necessary communication paths.
- We use Caddy as a reverse proxy for encrypted and authenticated access to otherwise insecure smart home services.
Firewall Rule Organization
- We only use floating rules that apply to all interfaces in order to have everything in one place.
- We apply rules to the firewall’s inbound interfaces only.
Firewall Mode of Operation
The following points summarize how the OPNsense firewall operates. It should help understand the rule logic.
- All incoming packets are blocked unless explicitly allowed.
- All outgoing packets are allowed unless explicitly blocked.
- As a stateful firewall, OPNsense automatically allows return traffic related to an established session.
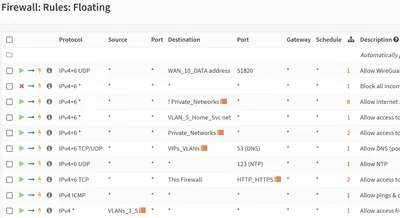
Firewall Rules
The following rules are sorted by descending order of precedence in the same way they’re displayed in the OPNsense UI.
Some of the rules use aliases or groups the definitions of which are listed further down.
Allow WireGuard VPN
This rule allows WireGuard VPN traffic from the WAN interface (= internet) to the firewall. If you’re running WireGuard on your OPNsense firewall and have it connected directly to the internet as I do this is the only firewall config you’ll need for WireGuard. Port forwarding, for example, is not required.
- Action: Allow
- TCP/IP version: IPv4+6
- Protocol: UDP
- Destination:
WAN_10_DATA address - Destination port: 51820
- Interfaces:
WAN_10_DATA
Block Incoming Internet Traffic
This rule blocks all incoming internet traffic not allowed by a rule with higher precedence (listed above this one).
- Action: Block
- TCP/IP version: IPv4+6
- Interfaces:
WAN_10_DATA
Allow Outgoing Internet Access
This rule allows internet access from all firewall interfaces added to it. It works by allowing all destination IP addresses that are not private network addresses.
- Action: Allow
- TCP/IP version: IPv4+6
- Destination:
not Private_Networks - Interfaces: Add all (VLAN) interfaces here from which you want to allow internet access.
Allow Access to Home Servers
This rule allows access from select internal VLANs to your home server VLAN. I only add my user VLAN to this, explicitly denying guests access to my home’s server services.
- Action: Allow
- TCP/IP version: IPv4+6
- Destination:
VLAN_5_Home_Svc net - Interfaces: Add all (VLAN) interfaces here from which you want to allow access to your home server(s).
Full Internal VLAN Access
This rule allows full access to all internal VLANs. It should be limited as much as possible. You should not include the user VLAN here. Instead, proxy access from the user VLAN to your internal (home) services via Caddy.
- Action: Allow
- TCP/IP version: IPv4+6
- Destination:
Private_Networks - Interfaces: I only allow this for the interfaces
VLAN_5_Home_Svc netandLAN_All.
Access to OPNsense’s DNS Server
This rule allows access to the DNS server service provided by OPNsense. It’s bound to all internal (!) interfaces. Make sure not to add the WAN (internet) interface, or your DNS server will be publicly accessible - a situation most providers won’t tolerate.
- Action: Allow
- TCP/IP version: IPv4+6
- Protocol: TCP/UDP
- Destination:
VIPs_VLANs - Destination port: 53 (DNS)
- Interfaces:
DNS_allowed
Access to the OPNsense Web UI
This rule allows access to the OPNsense web UI from select VLANs.
- Action: Allow
- TCP/IP version: IPv4+6
- Destination:
This Firewall - Destination port:
HTTP_HTTPS - Interfaces: I allow this on the
LAN_Alland theVLAN_9_Userinterfaces.
Pings & ICMP Messages
This rule allows pings and other types of ICMP messages.
- Action: Allow
- TCP/IP version: IPv4
- Protocol:
ICMP - Interfaces: I allow this on all internal interfaces except the guest VLAN (and the WAN interface).
Interfaces, VLANs, Aliases, and Groups
Interfaces
The following lists the firewall interfaces referenced in the rules above.
LAN
This is the physical LAN interface of the firewall host.
- Name:
LAN_All
WAN
This is the PPPoE connection to the internet my provider (NetCologne) requires for its FTTH offering (details).
- Name:
WAN_10_DATA - Type: PPPoE
VLANs
The following is not a complete listing of my VLANs but rather intended as an overview to help understand the principles I use to organize and segment devices.
Home-Infra (4)
This is my VLAN for (smart) home infrastructure devices such as a KNX IP gateway or the solar inverter. These types of devices often are inadequately secured, offering only unencrypted HTTP and/or unauthenticated access. By placing these devices in their own VLAN I can prevent direct connections. Instead, I provide access via my Caddy reverse proxy which also enforces SSO authentication.
- OPNsense name:
VLAN_5_Home_Infra - VLAN ID: 4
Home-Svc (5)
This is my VLAN for home server services such as Caddy, Samba, or Home Assistant. Devices in this VLAN can be accessed from the user VLAN. Access to devices in other VLANs (such as Home-Infra) is proxied through Caddy.
- OPNsense name:
VLAN_5_Home_Svc - VLAN ID: 5
User (9)
This is my VLAN for the PCs and phones from home residents. Devices in this VLAN can access the Home-Svc VLAN as well as the internet.
- OPNsense name:
VLAN_9_User - VLAN ID: 9
Guest (12)
This is my VLAN for devices from visitors. It only provides internet access. Connectivity to devices in other VLANs is blocked.
- OPNsense name:
VLAN_9_User - VLAN ID: 12
Aliases
This is a listing of the OPNsense aliases I used in the firewall rules described above.
Private Networks
This alias covers all private IP ranges not valid on the internet.
- Alias name:
Private_Networks - Alias content:
192.168.0.0/16172.16.0.0/1210.0.0.0/8169.254.0.0/16fe80::/10fc00::/7
Firewall Virtual IPs in all VLANs
This alias includes all virtual IPs (VIPs) of the OPNsense firewall in all VLANs.
- Alias name:
VIPs_VLANs - Alias content: I include all firewall IP addresses in all internal VLANs.
Interface Groups
This is a listing of the OPNsense interface groups I used in the firewall rules described above.
DNS Allowed
This group includes all interfaces where the firewall’s DNS service should be allowed to respond.
- Group name:
DNS_allowed - Members: All internal VLANs except (!) the WAN VLAN.






Comments