Terms Before Download
Terms Before Download is a Wordpress plugin that shows a popup dialog with terms and conditions (EULA) that must be accepted before a file can be downloaded.
Its most important features are:
- The terms and conditions are read from a WordPress page. That way there is only a single place to maintain the terms and they can easily be displayed independently of the plugin.
- It supports Google Analytics to keep track of the number of downloads.
- It is highly customizable.
The plugin is available in the official wordpress.org plugin directory. You can try it out here. This is what the plugin looks like:
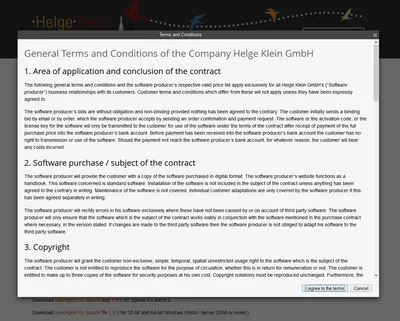
Comments