Finding (Executables in) User-Writeable Directories
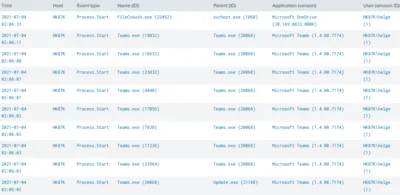
This article presents two different detection types for insecure filesystem permissions on Windows endpoints: scanning for directories that are user-writable, and detecting processes that are started from user-writeable directories.
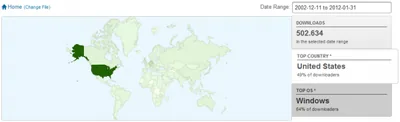
Directory Scan With ListUserWriteableDirectories & SetACL My ListUserWriteableDirectories script is an implementation of the first detection type: it scans the filesystem listing any permissions not known to be safe.
Security