Visualizing the Impact of Folder Redirection – Start Menu Search

This is the third in a series of articles on folder redirection by Aaron Parker, Helge Klein and Shawn Bass.
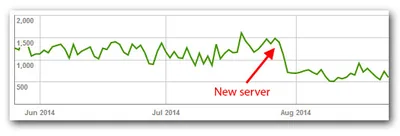
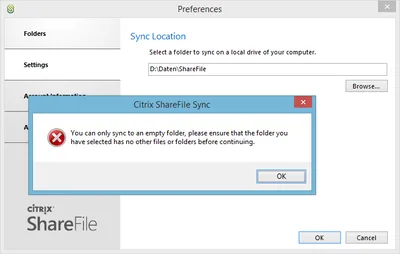
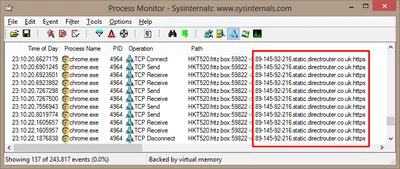
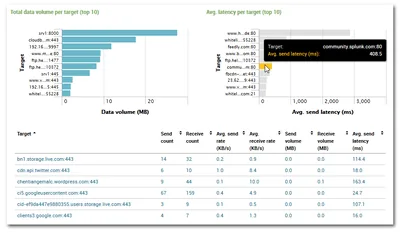
Part one: How Folder Redirection Impacts UX & Breaks Applications Part two: Visualizing the Impact of Folder Redirection – Logon and Application Launch Part three: this article Part four: Measuring the Impact of Folder Redirection – User Logon Previously on this Series If you have been following this mini-series you know that after explaining the basics in part one we got to the juicy bits in part two, where Aaron Parker presented videos that vividly show that folder redirection indeed speeds up user logons considerably, but at the price of potentially horrible user experience during the session. In this third part we are going to explore that in more detail.
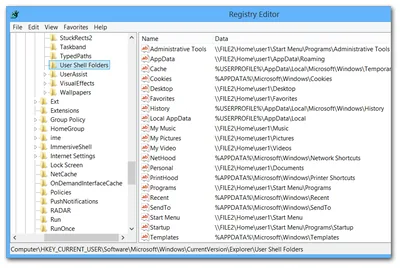
Windows Internals