Split-Tunnel VPN & WiFi: No Internet via IPv4 Due to Interface Priority

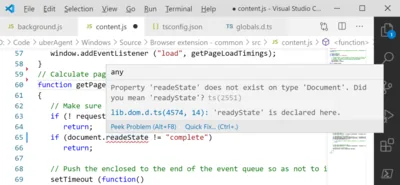
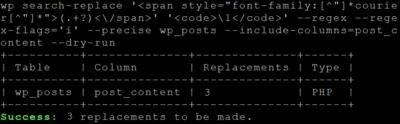
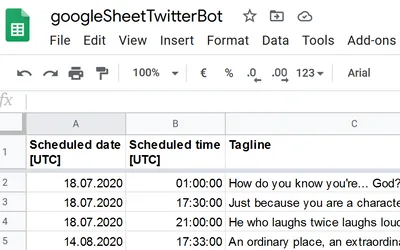
I had a weird issue on my laptop: whenever I connected to our company’s VPN, I lost local internet connectivity. As it turned out, this was caused by incorrect network interface priority metric settings. To spare you and my future self many frustrating hours of troubleshooting, here’s what caused it.
Networking