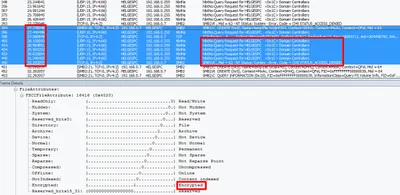
Which Software Installed That Driver - And When?
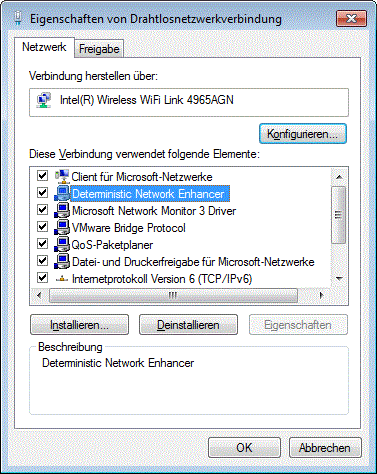
Installing a software that includes a driver may leave your system in an inconsistent state. If the install fails, parts may remain on the system. And if the remaining part is a driver, I get nervous - drivers are not the kind of stuff I want to have lingering around my system’s memory. Here is a way of identifying when a driver actually got installed.
Windows Internals