Find in Files With Grep-Like Context (Lines Surrounding Matches)
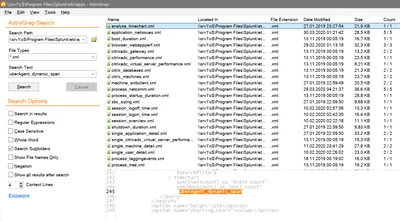
I sometimes need all occurrences of a search string in the files of a directory. OK, that’s easy. Here’s the difficult part: I need search results displayed with context around the matching lines. In other words: I need to know what is in the lines above and/or below the results. None of the text editors and IDEs I am using regularly seem to be able to do display search results with context lines. Enter AstroGrep.
Tips and Tools