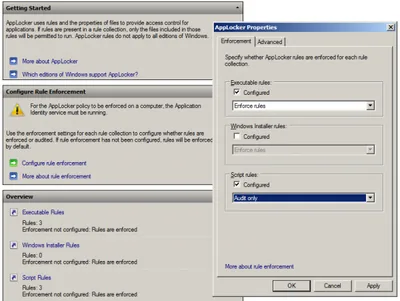
DNS Exfiltration & Tunneling: How it Works & DNSteal Demo Setup
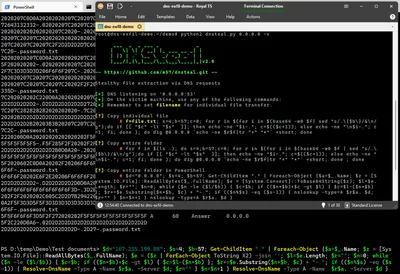
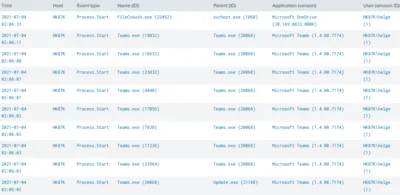
DNS is a protocol that lends itself to abuse because it’s largely unmonitored and unrestricted. This article explains how data exfiltration from a corporate network via DNS works and shows how to set up a working exfiltration demo with DNSteal.
Security