WLAN Security - Beware of (Unknown) Wi-Fi Hotspots
- Security
- Published Jan 3, 2012 Updated Jan 2, 2012
In its issue 1/2012 German c’t magazine published an article about security in Wi-Fi networks. The authors describe how very easy it is to gain access to other people’s accounts and passwords in a world where travelers happily connect to any wireless network they can get hold of. This is a short summary of the original article, intended to highlight the dangers.
The attacks described here are made possible by the following:
- For reasons of ease of use, public Wi-Fi networks often do not use encryption, e.g. WPA2. Data is literally flowing through the air completely unprotected.
- Even in encrypted networks communication between individual computers is often not disabled, making ARP spoofing attacks possible.
- The WLAN standards do not include any functionality to authenticate an access point. Wireless networks are identified by name only which makes it trivial to set up a fake “Telekom” network, for example.
Attack #1: Information Sniffing
NetworkMiner uses the capture driver WinPcap (known from Wireshark) to extract data from a (wireless) network. It fully automatically stores all images, other files, cookies, usernames and passwords:
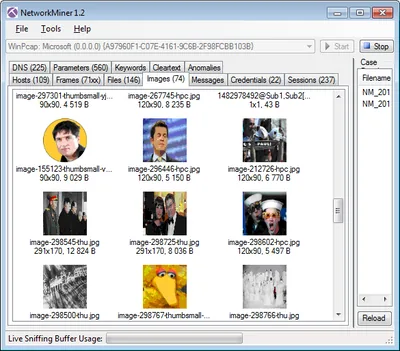
Setting up this attack is more than trivial: download and install WinPcap and NetworkMiner. Join any public wireless network. Run NetworkMiner and wait.
Attack #2: Account Hijacking
DroidSheep works similarly to Firesheep but runs inconspicuously on a smartphone. It captures session cookies from most sites and injects them in the attacker’s browser, making identity theft a matter of a single tap on a touchscreen.
Setting up this attack is easy: root your Android phone, install DroidSheep, join any public wireless network and run DroidSheep. As soon as another user on the network accesses a website requiring authentication, you are “in”. You can use that site with the other guy’s account, read messages, post status updates or steal the account by changing e-mail address and password.
Attack #3: Honeypot
An even easier way for capturing other people’s data than connecting to the Wi-Fi they use is to make them connect to you. To set this up, enable the mobile hotspot functionality of your Android phone and choose a name used by a popular hotspot provider. In Germany that could be “Telekom”. Then install a network packet capturing tool like “Shark for Root” which is tcpdump with a simple UI. That is all.
Other smartphones which have connected to the network called “Telekom” in the past will connect to your access point automatically. All internet traffic of those devices will be routed through your phone. Unencrypted data can easily be extracted from the captured traffic afterwards.
Remedy
Unfortunately, there is no real remedy as long as the WLAN standards lack significant security features like access point authentication. Here is what you can do today:
- Use UMTS (3G) instead of Wi-Fi.
- Only use known secure Wi-Fi networks, e.g. at home and at work.
- If you operate a Wi-Fi network, prohibit communication between endpoints.
- Create a guest Wi-Fi network which is separated from the internal production network.
- Use SSL/TLS encryption wherever possible. Unfortunately, many websites switch to unencrypted HTTP after the login making account hijacking by cookie theft trivial. Even worse, with smartphone apps there is practically no way to determine whether they communicate securely or not.
c’t explicitly does not recommend to use a VPN with a smartphone because the combination simply is not safe: after a temporary connectivity loss the internet connection via WLAN or 3G is restored automatically, but the VPN connection is not.






Comments