AppLocker - Solutions to Common Problems
- Security
- Published Aug 22, 2012 Updated Nov 17, 2019
This article is part of my small series about AppLocker, a technology built into Windows that enables administrators to audit and optionally block application execution.
AppLocker and UAC
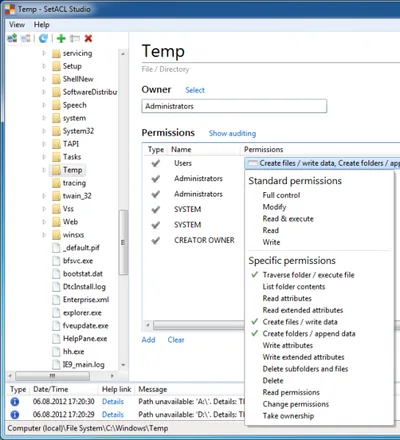
One of the default rules allows unrestricted application execution for administrators. That is only sensible. After all, someone needs to be able to troubleshoot and perform maintenance. However, if UAC is enabled, that rule is not very useful. Remember: UAC filters the SID for the group Administrators from the access token during normal operation. With the Administrators’ SID gone, AppLocker is active for administrators in the same way it is for all other users. Administrators wishing to bypass AppLocker need to start executables from an elevated command prompt (or right-click and select run as administrator), which is often impractical.
Here is a nice way to shoot yourself in the foot: block an application that requires elevation. As an admin, execution should be allowed, right? Wrong. The only thing you get when you double-click the executable is an error message. If you want to run the application you need to run it elevated, e.g. by right-clicking and selecting run as administrator from the context menu.
Recommendation: add a path rule that allows execution for a special NoAppLocker domain group (use an asterisk (*) for the path). You can then add users to that group as necessary without even having to make them members of the local Administrators.
 by [Beyond Elements](http://www.flickr.com/photos/micromitra/) under [CC](http://creativecommons.org/licenses/by/2.0/deed.de)](/images/2012/08/generated/Lockers-600x397_400w.6c6099f224887ab14aee962693a6b8266b1bf1b2b8cdfdfe3b642efcae085d2f.webp)
More Recommended Rules
General
- Path rule to allow execution from the Windows directory for everyone
- Path rule to allow execution from the Program files directories for everyone. You can use the (AppLocker, not environment!) variable
%PROGRAMFILES%which applies to both program directories on an x64 system (C:\Program Files and C:\Program Files (x86)). - Path rule to allow execution from the
\\domain\sysvol\domain\policiesdirectory for everyone (to allow the execution of logon scripts)
App-V
- Path rule to allow execution from the Q: drive for everyone (if App-V 4.x is used; with App-V 5 this is not necessary any more)
- App-V SCRIPTBODY scripts are executed from batch files created on the fly and stored temporarily on the hard disk. Add a script path rule to allow execution of
C:\Users\*\AppData\Local\Softgrid Client\*\*.bat
VPN Client Software
Software like the Aventail VPN client installs in user context from the web browser. This works by downloading to and executing files from the user’s temp directory, which would be blocked by AppLocker without additional configuration.
The temp directories are located inside the user profiles and writeable by the user; adding a path rule for temp is not exactly desirable from a security point of view. Instead of allowing execution of anything from a specific path we can allow execution of anything from a specific vendor: configure a publisher rule that allows execution of all files digitally signed by the VPN client software vendor.
Printer Drivers
The installation of printer drivers for users without administrative rights can be enabled easily by adding the GUID {4d36e979-e325-11ce-bfc1-08002be10318} to the policy Computer Configuration\Policies\Administrative Templates\System\Driver Installation. That, however, is only part of the solution. Most printer drivers are packaged as executables - whose execution is blocked by AppLocker, of course. If end users are to install arbitrary printer drivers on their own publisher rules need to be configured that allow the execution of programs from specific vendors. Please note that:
- one such rule is required per vendor (Canon, HP, Epson, Lexmark, Kyocera, …)
- the rule allows the execution of all digitally signed files from that vendor
- files that are not digitally signed are still blocked
Resources
AppLocker Technical Documentation for Windows 7 and Windows Server 2008 R2





Comments