uberAgent UXM
uberAgent UXM covers all aspects of digital employee experience (DEX). It tracks the reliability and performance of any physical or virtual machine, enabling enterprise IT to provide productive digital work environments.
uberAgent is more than just monitoring. It is an indispensable tool for all phases of the IT lifecycle, from analysis to design, implementation, operations, and troubleshooting. uberAgent helps IT pros understand end-users without invading their privacy.
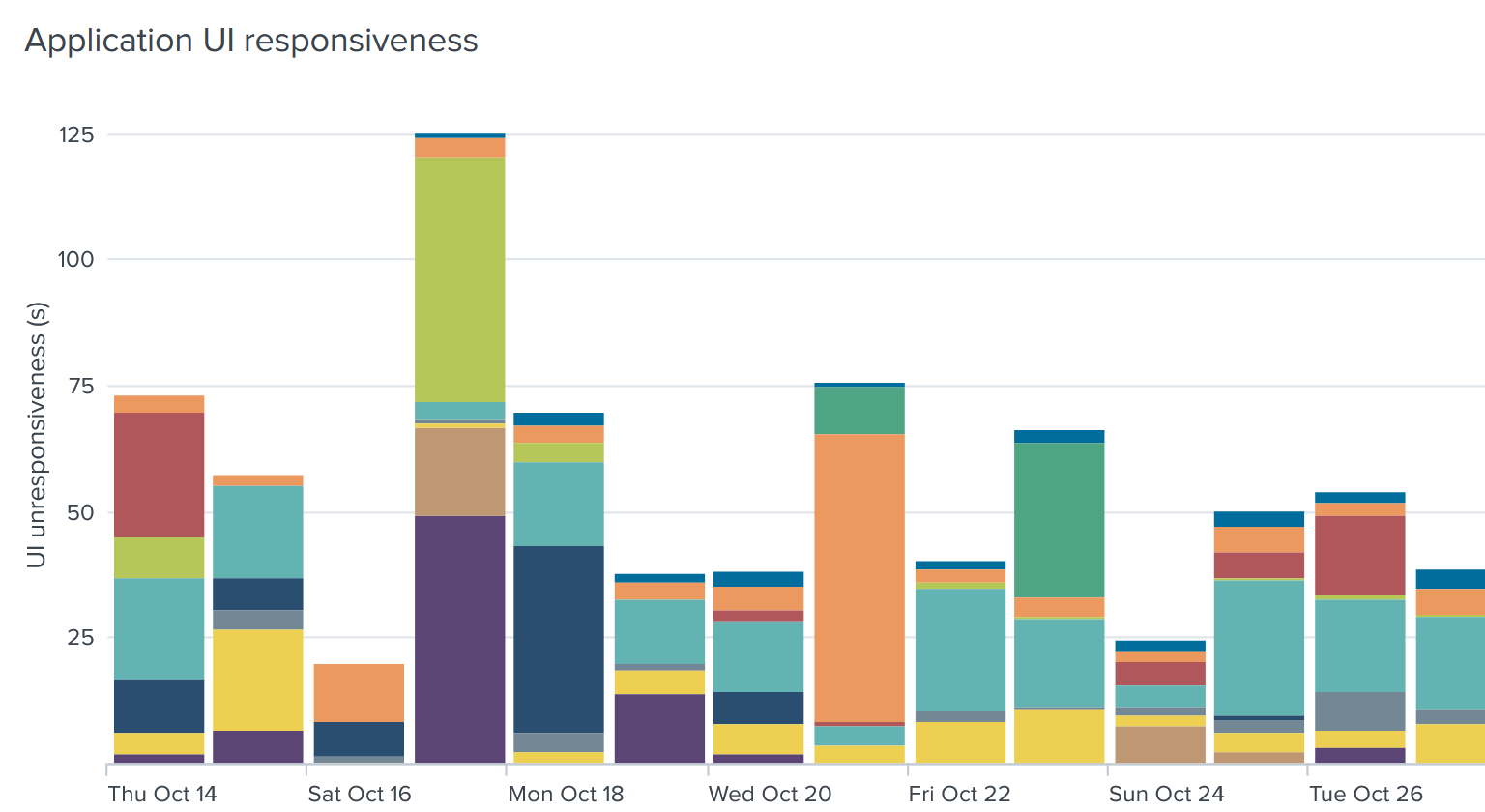
- Application reliability
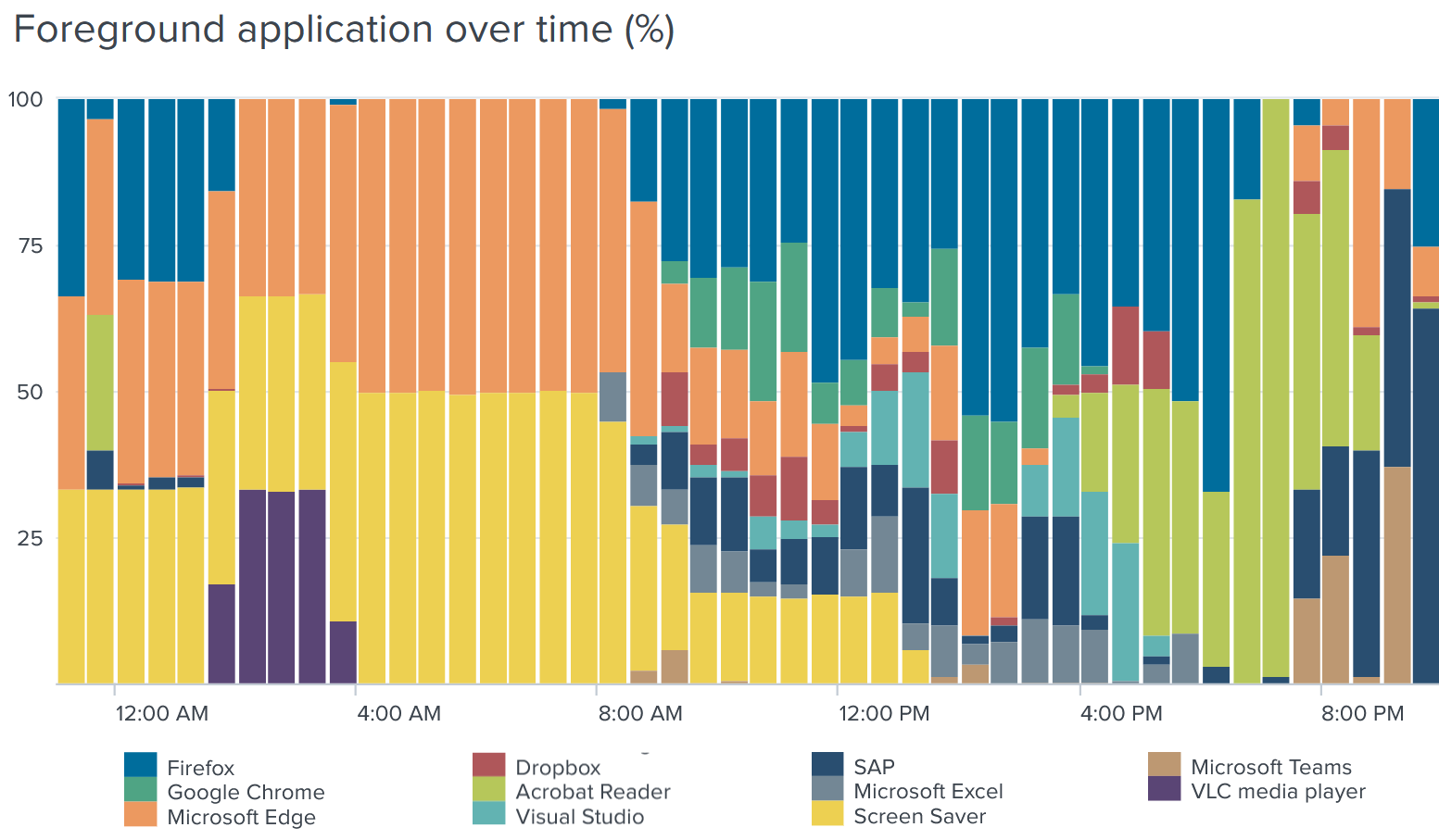
- Browser usage
- Citrix optimization
- Network diagnostics
- OS performance
- Web app troubleshooting